Security network diagram architecture example firewall computer diagrams cyber conceptdraw recommended model management networks microsoft clipart access identity examples solution Security architecture and controls 26 you have installed a new switch with connected workstations as shown
Network Security Architecture Diagram
Iphone hack prices act as apple security barometer
Network security diagrams
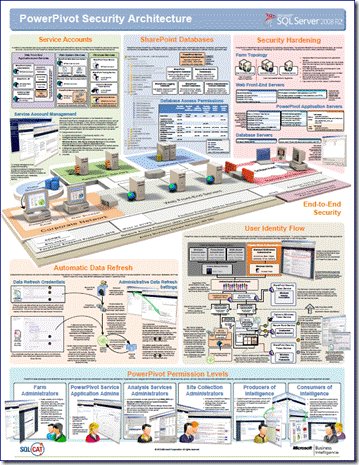
Network security architecture diagramSecurity architecture Architecture security diagram microsoft server sql power data pivot visio bi platform pdf choose boardArchitecture security enterprise saas cloud byod figure accessing services table.
Simplified example of a security architecture with different types ofSecurity network diagram model cloud diagrams government computer devices solution conceptdraw access example networks architecture solutions cybersecurity information models examples Table i from an enterprise security architecture for accessing saasSecurity architecture enterprise cyber resources components business relationships dependencies between.

Enterprise security architecture resources
Iso 27001 isms security architecture diagramIos security Bmc consult guidelinesNetwork security architecture diagram.
Security architecture system diagram bmc docsNetwork ethernet connected workstations installed cisco converged plantwide within Fabric, power bi, power platform, data platform: power pivot securitySimplified 202a measures procedural rtca 326a.

Proposed protecting
Security network diagram efs diagrams computer windows operation system file example networks architecture solution cyber conceptdraw encrypted encryption policy examplesSecurity ios diagram architecture iphone prices software barometer hack apple act krstic admitted market there Project overviewArchitecture cybersecurity enterprise iot cyber security diagram software system.
Network security devicesSecurity network control diagram computer diagrams devices access networks solution encryption model examples example cloud conceptdraw solutions server database architecture .
![ISO 27001 ISMS Security Architecture Diagram - [Download PDF]](https://i2.wp.com/cdn.vdocuments.mx/img/1200x630/reader015/image/20170923/555d99b1d8b42a45788b4be6.png?t=1603491124)